Requirements
- EKS cluster (deployed in the last step here) deployment completed.
- Kubectl configured with access to the EKS cluster.
- Helm.
Install the Sysdig Agent
The next steps will deploy the Sysdig Agent in all the nodes of the EKS deployed during the prerequisites step.
-
Log into Sysdig Secure, and browse to Integrations > Data Sources > Sysdig Agents, then Connect a Kubernetes Cluster. Insert a cluster name of your choice (for example
aws-workshop) and copy the resulting command.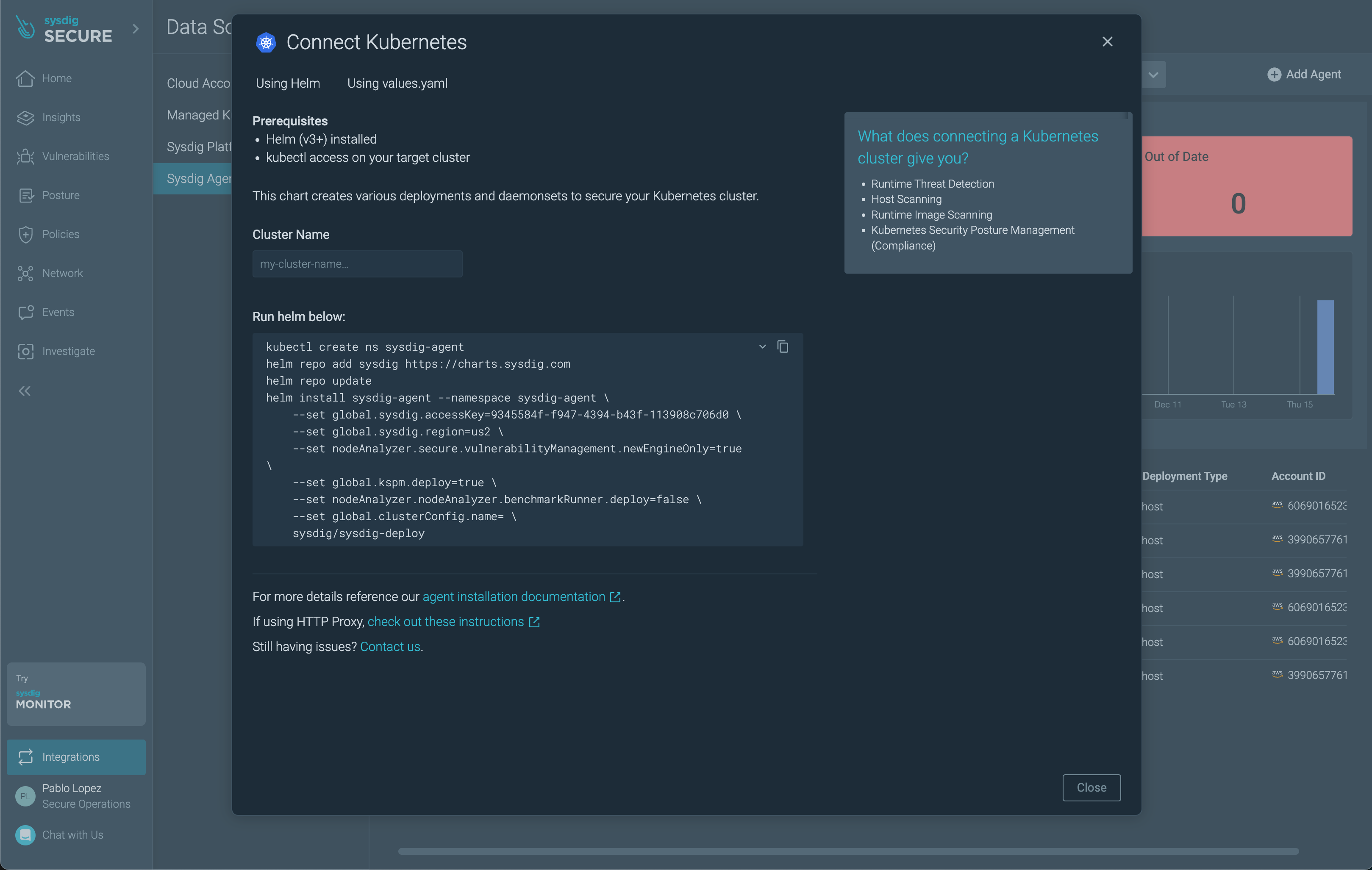
-
The Sysdig’s Admission Controller (AC) for Kubernetes is not deployed by default. This component enables the Kubernetes Audit Logging Capabilities of Sysdig Secure among other features (for example, vulnerability management for your k8s images).
In your IDE, add the next parameters to the Helm command copied above and update the secureAPIToken value with your API Token available in your account Settings (remember to add the trailing
\at the end of the new options):--set admissionController.enabled=true \ --set admissionController.sysdig.secureAPIToken=9345f4k3-f4k3-f4k3-f4k3-f4k308c706d0 \ --set admissionController.features.k8sAuditDetections=true \ --set scanner.enabled=false \ -
Execute the resulting command in your terminal. The Sysdig Agents are being deployed now on each of the nodes of the cluster.
helm repo add sysdig https://charts.sysdig.com helm repo update helm install sysdig-agent --namespace sysdig-agent --create-namespace \ --set global.sysdig.accessKey=9345f4k3-f4k3-f4k3-f4k3-f4k308c706d0 \ --set global.sysdig.region=eu1 \ --set nodeAnalyzer.secure.vulnerabilityManagement.newEngineOnly=true \ --set global.kspm.deploy=true \ --set nodeAnalyzer.nodeAnalyzer.benchmarkRunner.deploy=false \ --set global.clusterConfig.name=aws-workshop \ --set admissionController.enabled=true \ --set admissionController.sysdig.secureAPIToken=94be24b3-eaf9-4951-996d-79545cfe1089 \ --set admissionController.features.k8sAuditDetections=true \ --set scanner.enabled=false \ sysdig/sysdig-deploy
Sysdig Secure Policies
When the installation is complete, visit the Runtime Policies section and filter the list of policies by type: Kubernetes Audit. Then, enable the Sysdig K8s Activity Logs and Sysdig K8s Notable Events policies. These policies will alert about each and every K8s Audit Event in your EKS cluster.

After this, filter too by:
AWS CloudTrailand enable all the available policies.Workloadand enable all the available policies.
Create a new policy, select type Worload Policy.
From the rule library, add the rule: Write below etc
name it aws-workshop-test-policy, add a description foo
and enable Captures.
Review installation
Agents
Check that the Agent installation was successful in the Integrations > Data Sources > Sysdig Agents section.

The EKS cluster will also be visible in the Managed Kubernetes section.

Alternatively, you can check the logs of the agent pod:
kubectl logs -l app.kubernetes.io/name=agent -n sysdig-agent --tail=-1 | grep "Sending scraper version"
Admission Controller
Check that the Admission Controller installation was successful by generating an event that will be registered in the k8s API:
-
Trigger some events with:
kubectl exec -n sysdig-agent \ $(kubectl -n sysdig-agent get pod -l app=sysdig-agent \ --output=jsonpath={.items..metadata.name} \ | cut --delimiter " " --fields 1) -c sysdig -- ls /bin/ > /dev/null kubectl run nginx --image nginx --privileged -
Then, visit the Events section and it will show up after you select the Info level.

-
Alternatively, check the admission-controller pod logs:
kubectl logs -f -n sysdig-agent \ -l app.kubernetes.io/component=webhook \ --tail=-1 --follow=falseEvery action against the K8s API Server will generate an entry in the logs (based on the configured logging level). You should see something like this:
... {"level":"info","component":"console-notifier","time":"2022-12-15T15:20:11Z","message":"Pod started with privileged container (user=kubernetes-admin pod=222nginx111 ns=default images=nginx)"} ...