Push and Scan images on ECR
Download Example Dockerfile and Sources
Now that our automated scanner is in place, we can test it by pushing a Docker container, and check if it scans.
To illustrate the images scanning we will build an example Node.JS application based on the official “hello world” example described in their website.
-
Go to your Cloud9 Workspace and download and uncompress example container files:
wget https://github.com/johnfitzpatrick/hello-world-node-vulnerable/archive/v1.2.zip unzip v1.2.zip cd hello-world-node-vulnerable-1.2 -
And build and push the image to ECR
AWS_ACCOUNT=$(aws sts get-caller-identity | jq '.Account' | xargs) export ECR_NAME=aws-workshop export REGION=us-east-1 export IMAGE=$AWS_ACCOUNT.dkr.ecr.$REGION.amazonaws.com/$ECR_NAME docker build . -t $IMAGE docker push $IMAGE -
For every new event of an image pushed to the registry, Sysdig executes an image scan using the integrated Sysdig Inline Scanner.
-
Wait a few seconds to access the scan results in Sysdig Secure. Meanwhile, you can check the logs of the scanning process in AWS by visiting: CloudWatch > Log groups.
There, click on:
- Log group: sfc-cloudconnector…
- Log stream: ecs/CloudConnector/…
Once all the logs are presented, filter by
scanand observe the events signaling the status of the scan.This is not the main method to observe scan results, but an advanced tip to learn more about the process status.
See Scan Results on Sysdig Secure Dashboard
To see the scan results on Sysdig Secure Dashboard,
-
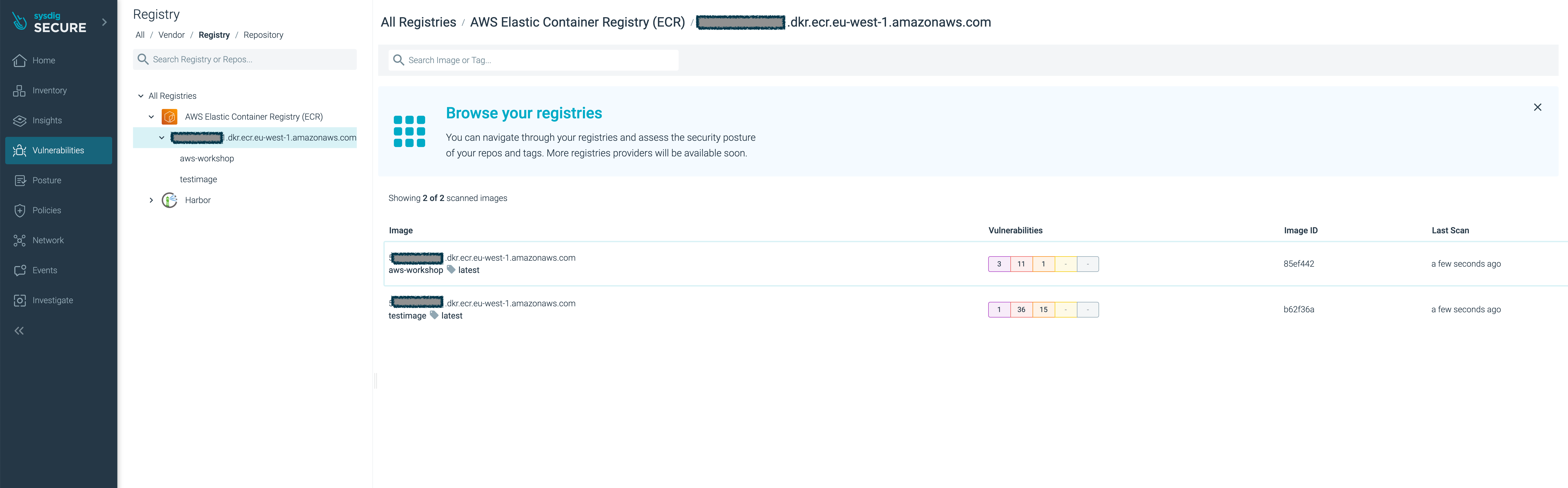
Log into the Sysdig Secure UI, and browse to Vulnerabilities > Registry:
-
Click your new
aws-workshopimage.You’ll see the image have several major vulnerabilities.
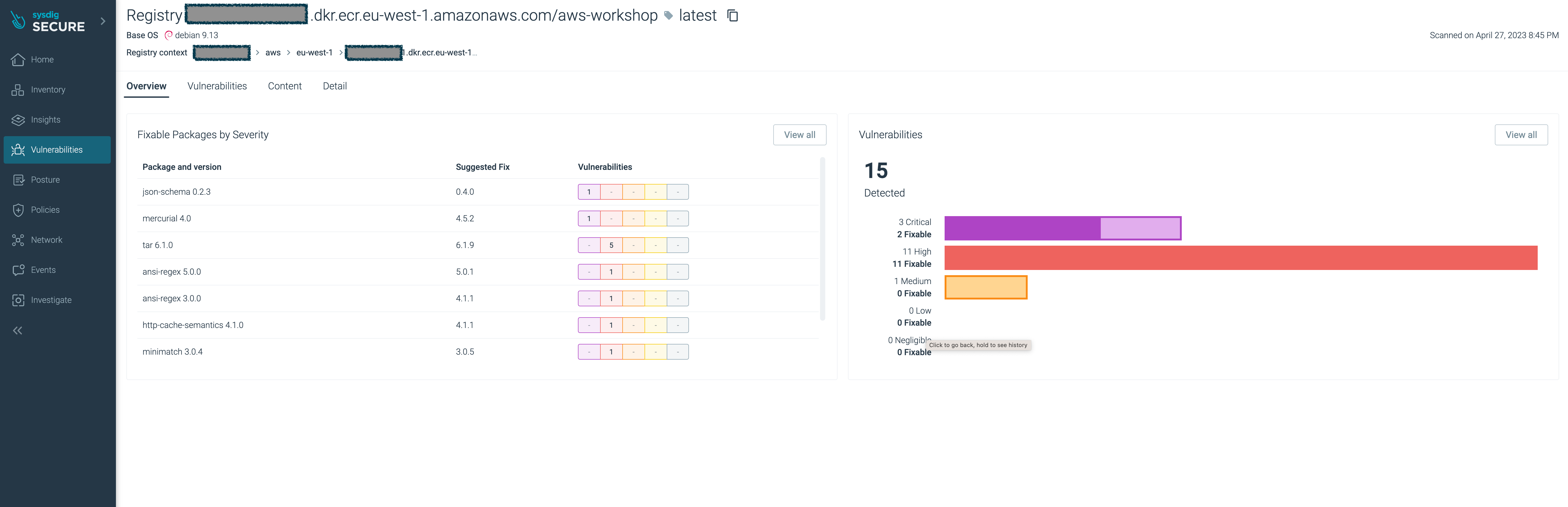
With Sysdig Secure you have full visibility of the security and compliance posture across your entire estate, in a single pane of glass, and as a central location for all security profiles and policies.
ECR Scanner: event-based vs full-scan
Sysdig provides multiple methods to adjust to your use case.
The steps described above will scan images for every new push event to an ECR registry.
It is also possible to deploy and schedule the scanner to scan the registry with a cronjob.
To learn more about this method, visit the chart documentation for the Registry Scanner.
This method will be the main approach for ECR image scanning when the feature gets to GA.
Digging deeper
The sysdig-cli-scanner is a binary that you can integrate in multiple stages of your build pipeline You can even execute it locally to run a quick scan of an image you just built. Let’s see how to do this:
-
In your terminal, set two environmental variables with your Sysdig account API credentials:
export SECURE_API_TOKEN=b7788d43-f4k3-f4k3-f4k3-d0c0edfb526e export SYSDIG_SECURE_ENDPOINT=https://app.au1.sysdig.com/secure/ -
Download the sysdig-cli-scanner and give exec permissions to it. Execute an scan with:
curl -LO "https://download.sysdig.com/scanning/bin/sysdig-cli-scanner/$(curl -L -s https://download.sysdig.com/scanning/sysdig-cli-scanner/latest_version.txt)/linux/amd64/sysdig-cli-scanner" chmod +x ./sysdig-cli-scanner ./sysdig-cli-scanner --apiurl $SYSDIG_SECURE_ENDPOINT $IMAGE -
The logs will provide an overview of the process:
2023-01-04T17:28:54Z Starting analysis with Sysdig scanner version 1.3.1-rc 2023-01-04T17:28:54Z Retrieving MainDB... 2023-01-04T17:28:55Z Done 129.0 MB 2023-01-04T17:28:55Z Loading MainDB... 2023-01-04T17:28:55Z Done 2023-01-04T17:28:55Z Retrieving image... 2023-01-04T17:29:21Z Done 2023-01-04T17:29:21Z Scan started... 2023-01-04T17:29:22Z Uploading result to backend... 2023-01-04T17:29:22Z Done 2023-01-04T17:29:22Z Total execution time 28.696292941s Type: dockerImage ImageID: sha256:8e8e32a51105f15ddc2523d72aad5fa5cd48d1072f4288474087ad708c430c67 Digest: sha256:b1ddc7482510ea70302785c5101bff882210e25f7727f150a3a66133cd5d6270 BaseOS: debian 9.13 PullString: 430768456966.dkr.ecr.us-east-1.amazonaws.com/aws-workshop 14 vulnerabilities found 3 Critical (2 fixable) 10 High (10 fixable) 1 Medium (0 fixable) 0 Low (0 fixable) 0 Negligible (0 fixable) PACKAGE TYPE VERSION SUGGESTED FIX CRITICAL HIGH MEDIUM LOW NEGLIGIBLE EXPLOIT json-schema javascript 0.2.3 0.4.0 1 0 0 0 0 0 mercurial python 4.0 4.5.2 1 0 0 0 0 0 tar javascript 6.1.0 6.1.9 0 5 0 0 0 0 ansi-regex javascript 5.0.0 5.0.1 0 1 0 0 0 0 ansi-regex javascript 3.0.0 5.0.1 0 1 0 0 0 0 minimatch javascript 3.0.4 3.0.5 0 1 0 0 0 0 path-parse javascript 1.0.6 1.0.7 0 1 0 0 0 0 qs javascript 6.5.2 6.5.3 0 1 0 0 0 0 POLICIES EVALUATION Policy: Sysdig Best Practices FAILED (22 failures - 0 risks accepted) Policies evaluation FAILED at 2023-01-04T17:29:22Z Full image results here: https://secure.sysdig.com/#/scanning/assets/results/17372b452b872f83f261d405ea65ba10/overview (id 17372b452b872f83f261d405ea65ba10) Execution logs written to: /home/ec2-user/environment/tf/hello-world-node-vulnerable-1.2/scan-logs -
Go to Vulnerabilities > Registry to observe the results.