View AWS Foundations Benchmark Security Posture
In this exercise we will check the security posture of our AWS cloud infrastructure and remediate a potential issue.
The initial scan will occur as soon as the integration is deployed with the CF template, and daily after that by default.
Log into Sysdig Secure, and Browse to ‘Compliance’ in the left menu, then click on ‘AWS Foundation Benchmarks’

You will notice along the top that this benchmark is using “CIS Amazon Web Services Foundations ComplianceBenchmark”
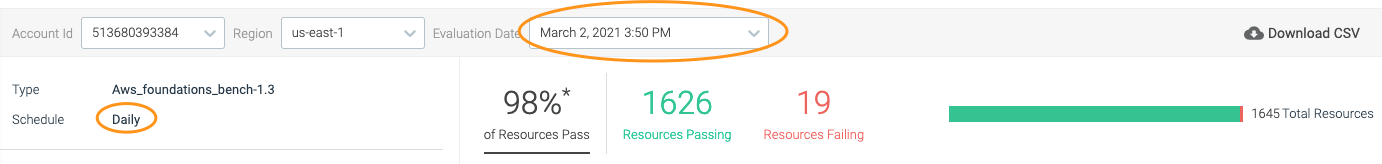
You’ll also see a brief synopsis of how compliant your system is against this benchmark, as well as a link to download the results as a CSV file.
Highlight 1.9 Ensure IAM password policy prevents password reuse under ‘Identity and Access Management’
You will notice that this resource is flagged as having failed. The reason this has failed is no password policy has been set in the account.
To verify no password policy has been set, go to your Cloud9 workstation and run the following command
aws iam get-account-password-policyYou will likely see an error such as This
An error occurred (NoSuchEntity) when calling the GetAccountPasswordPolicy operation: The Password Policy with domain name 128440595215 cannot be found.Expand the Remediation Procedure. You’ll see a number of manual remediation steps. Execute the command line fix
aws iam update-account-password-policy --password-reuse-prevention 24You can verify the change by rerunning the former command
aws iam get-account-password-policyThis should return content similar to the following
{ "PasswordPolicy": { "MinimumPasswordLength": 6, "RequireSymbols": false, "RequireNumbers": false, "RequireUppercaseCharacters": false, "RequireLowercaseCharacters": false, "AllowUsersToChangePassword": false, "ExpirePasswords": false, "PasswordReusePrevention": 24 } }The next time the scan occurs this control will now pass, and appear as follows
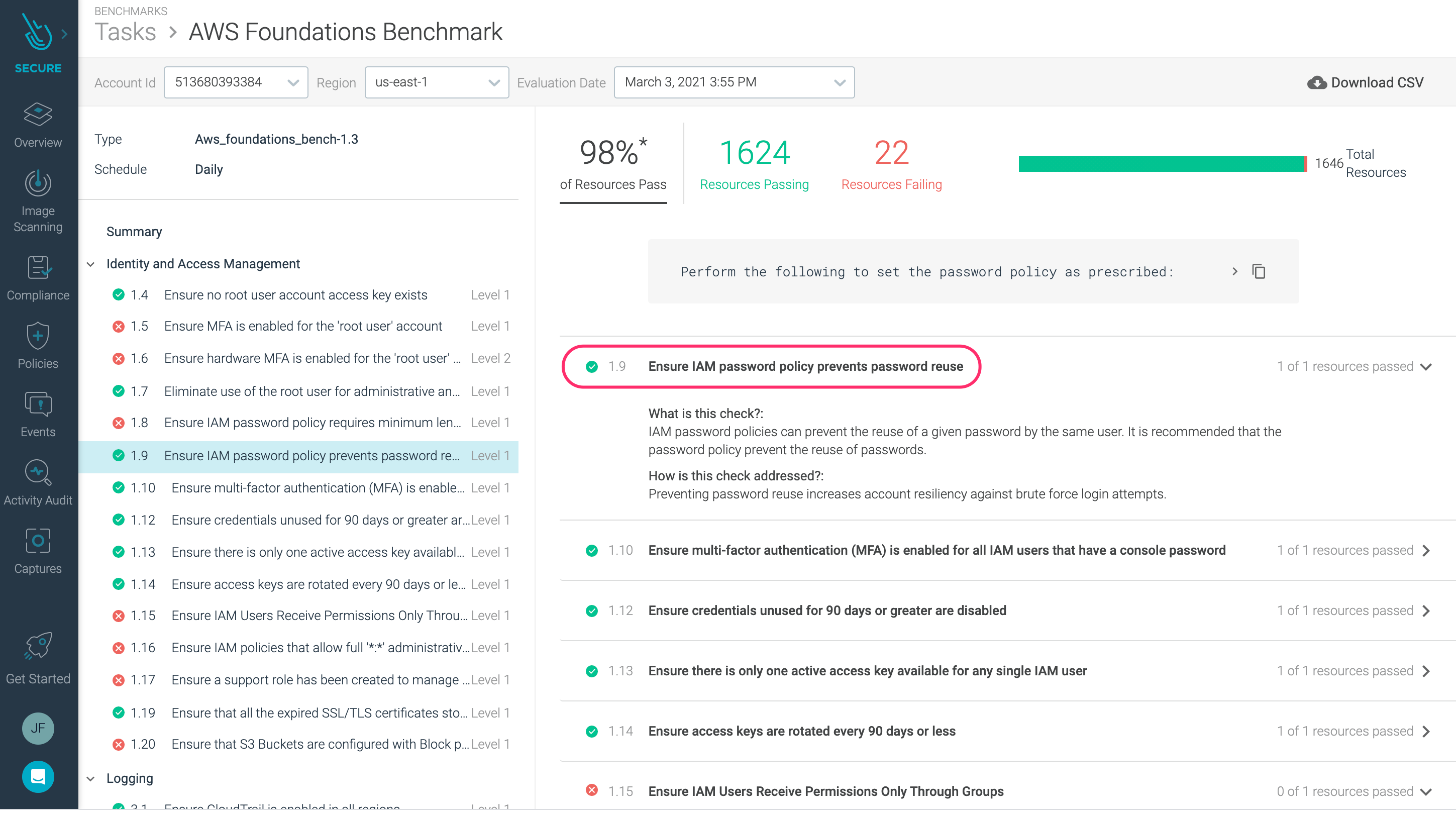
The scan runs every 24 hours.