Detecting Runtime Cloud Security Threats
Let’s look at an example of AWS threat detection in action with CloudTrail and the Sysdig CloudConnector. To do so we’ll create an S3 bucket, and make it public.
S3 bucket names are globally unique, so we’ll use your initials in lower case combined with a timestamp to formoudtrailssdsss the bucket name.
Log into Cloud9 Workspace, and set your initials as an environment variable
INITIALS=<your initials>Now create the S3 bucket, ensuring the bucket name is in lowercase.
BUCKETNAME="${INITIALS,,}"-$(date +%s) aws s3api create-bucket --bucket $BUCKETNAME --acl public-readNow delete the S3 bucket’s encryption. This should be considered a potential security threat.
aws s3api delete-bucket-encryption --bucket $BUCKETNAMEYou can view details of this event by browsing to CloudTrail then ‘Event History’
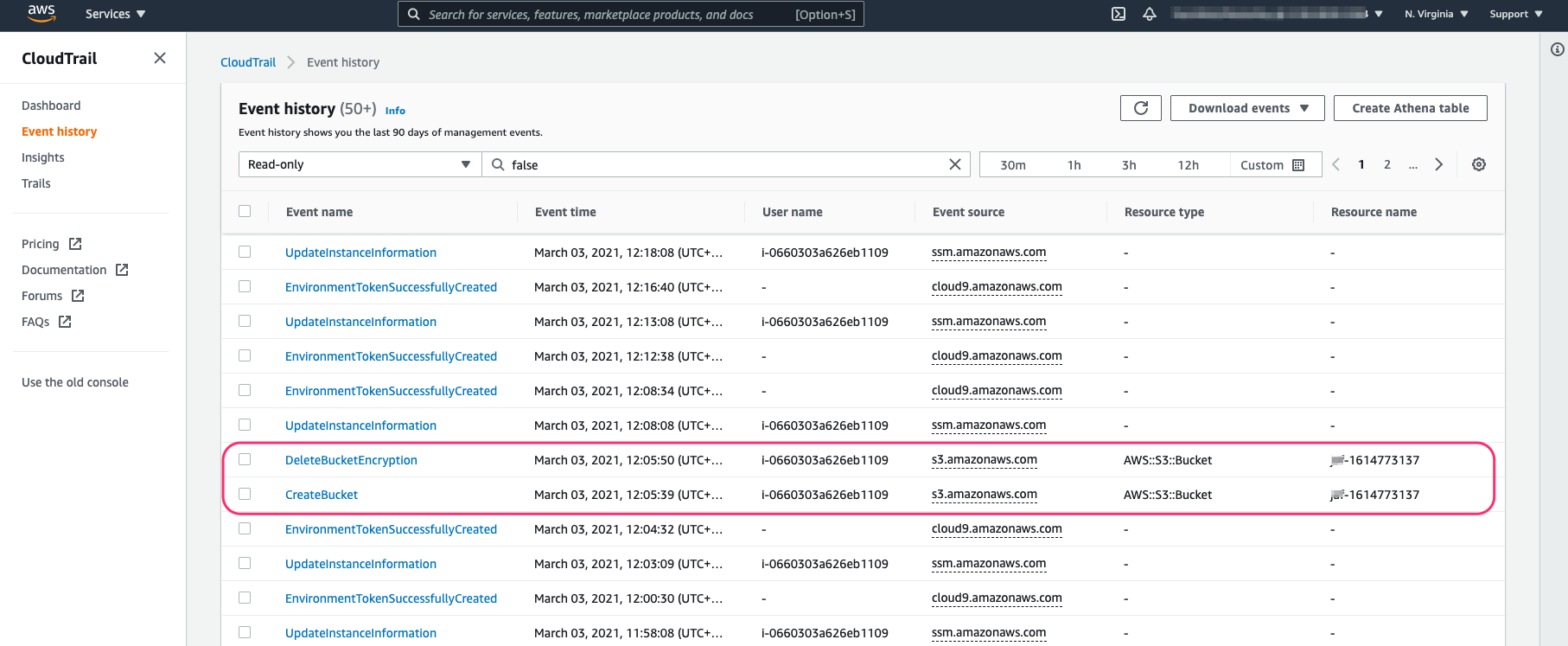
NOTE It can take several minutes for new events to appear in CloudTrail. In the meantime you can browse the existing events created earlier from earlier activity in the account.
If you scroll down you’ll see details of the new CloudTrail event in JSON format:

All CloudTrail events have the following key fields:
- userIdentity: The user who sent the request.
- eventName: Specifies the type of event.
- requestParameters: Contains all of the parameters related to the request.
The Falco rule should have triggered creating an event in Sysdig Secure, so we’ll look at that next.